TON Web Platforms
Initially, the network protocols were specifically designed for the TON blockchain to enable effective communication and data exchange between nodes. Today, the network offers solutions that are so robust and versatile that they collectively represent a new generation of internet infrastructure.
Even when considered separately from the TON blockchain, the TON network stands out as a fully decentralized, secure, and private computing network, similar to TOR or the I2P (Invisible Internet Project).
The TON network is intricately linked with the TON blockchain, its native Toncoin cryptocurrency, and various TON services. This integration creates a powerful synergy, advancing the network’s technology to unprecedented levels.
TON Network Features
- Decentralized: Operates as a peer-to-peer network without any centralized servers.
- Robust: The network remains functional even if some nodes go offline.
- Anonymous: Identifying a node’s IP address is either impossible or extremely challenging.
- Encrypted: All data transmitted between nodes is encrypted.
The network utilizes UDP/IP and TCP/IP protocols for internet communication. For a more in-depth technical overview of these protocols, refer to Chapter 3 of The Open Network’s white paper.
The TON blockchain relies on the TON network. Since the project’s launch three years ago, the nodes (including validators and servers) have effectively communicated through the TON network, demonstrating its stability and efficiency.
As blockchain operations grow in complexity, more advanced network solutions will be necessary. The TON network is well-suited to meet the demands of next-generation blockchains. For instance, when the TON blockchain scales into multiple sub-blockchains to handle high throughput, each sub-blockchain operates within its own dedicated sub-network.
TON Sites
The TON blockchain extends beyond just blockchain applications. From now on, you can set up a web server and host your site on the TON network—essentially creating a TON Site.
Mandatory Encryption and Data Authenticity Verification
In the early days of the internet, data exchanges—such as chat messages—were transmitted in plain text and could be intercepted by anyone on the network. There was no way to ensure that the data wasn’t altered during transmission.
The advent of HTTPS changed this by providing encryption and authentication for data.
Although HTTPS has become widespread over the past 15 years, approximately 20% of websites still do not use this protocol by default.
Consequently, there remains a risk that users’ data might be transmitted through unencrypted channels.
To address this, the TON network enforces mandatory encryption and automatically verifies the authenticity of all data traffic.
Eliminating the Need for Certification Authorities
To secure data and verify its authenticity, traditional websites require special certificates. While you can technically generate these certificates yourself, they may not be trusted as highly as those issued by certification authorities. These authorities, which may charge a fee or offer free services, are supposed to verify the site owner, but often even costly extended certificates lack proper diligence.
In essence, many certification authorities fall short of their responsibilities.
TON Sites simplify this by incorporating built-in cryptographic measures to ensure data encryption and authenticity. Your site will be secure immediately, without the need to engage with certification authorities.
Say Goodbye to Domain Name Registries

For traditional websites, domain names are rented from commercial entities, essentially centralized domain name registries.
A major issue with this system is that your domain name can be suspended or revoked for arbitrary or unknown reasons, or even by mistake.
Anyone can report to a domain name registry that your website is involved in illegal activities. Even if this claim is false, the registry’s staff might be forced to suspend your site without a full investigation into the situation, leading to significant trouble and financial losses.
TON Sites eliminates this problem by using TON DNS, a completely decentralized domain name system.
Unlike traditional registries, which require substantial payments to cover administrative costs, TON DNS only requires a minimal annual micropayment as a token of domain ownership.
Connecting a TON Site to a Domain

Subdomains
Just like with conventional websites, you can create subdomains for your TON Sites using TON DNS.
To achieve this, you can utilize any compatible smart contract.
We have developed several pre-built smart contracts for this purpose.
With the manual-dns smart contract, a site owner can assign any page to any subdomain.
For service providers, the auto-dns smart contract is available. This allows users to register their own subdomains by paying a network fee and an optional service fee.
For example, a social network like place.ton enables Alice to register a personal subdomain, such as alice.place.ton, by paying a small amount of Toncoin.
Additionally, you can conduct an auction for NFT subdomains, similar to the initial distribution of “.ton” domains.
TON WWW
Assigning a Wallet to Your Domain
Imagine you visithttp://foundation.ton and wish to contribute 10 TON to support network development. How would you proceed?
It’s straightforward: Simply transfer 10 TON directly from your wallet to the domain address. No additional payments or details are necessary.
The same applies to subdomains. For instance, if you visit Alice’s personal page at alice.place.ton on the place.ton social network, you can send 10 TON as a gift by entering alice.place.ton as the recipient address. Alice will receive the TON in her cryptocurrency wallet, which she linked to her account during its creation.
Authentication
On the traditional internet, users must register and create unique passwords for each site. This process can become cumbersome and inconvenient, even with the use of password managers. Many users resort to using the same password across multiple sites, which poses significant security risks.
Additionally, logging in often requires an email address or phone number, which can attract unwanted advertisements.
With TON, there’s no need for registration. You can log in to websites or applications using your TON-based crypto wallet, eliminating the need to share your email address or create multiple passwords for different services.
Hyperlinks
The World Wide Web consists of interconnected web pages where text can include hyperlinks. These links allow users to navigate seamlessly from one resource to another or to perform actions such as opening an email client.
TON Sites function similarly to traditional websites, but they are accessed through the TON network. Their URLs resemble those of regular websites but end with “.ton” — for example,http://foundation.ton.
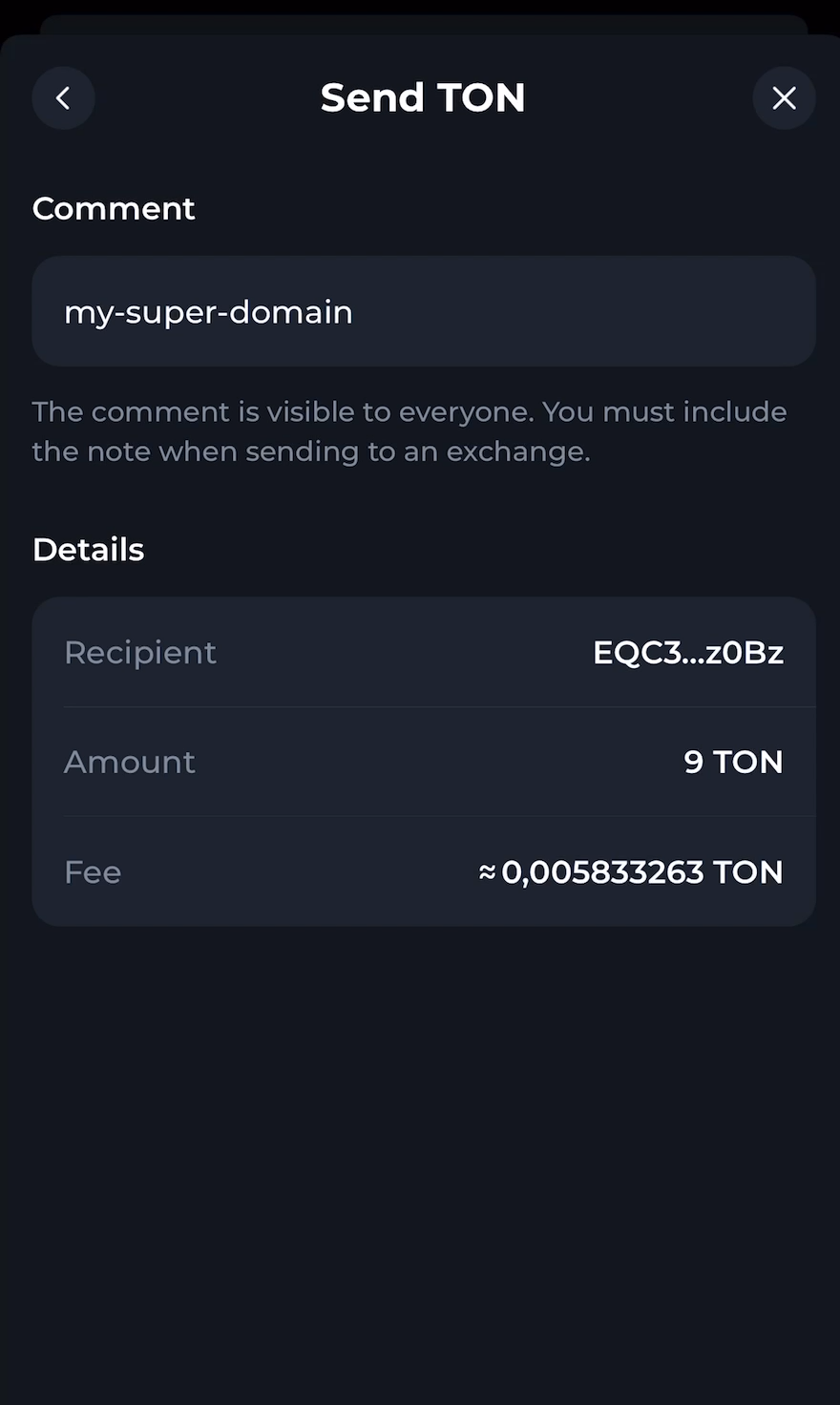
TON uses a distinct format for hyperlinks to trigger actions:
ton://domain/<method>?<field1>=<value1>&<field2>;..
For instance: ton://EQCD39VS5jcptHL8vMjEXrzGaRcCVYto7HUn4bpAOg8xqB2N/transfer?amount=1&text=hello
Clicking this link will launch the TON crypto wallet, pre-filling the recipient’s address, the amount of crypto, and any additional information.
Web developers can also create scripts that interact with your TON wallet or TON browser extension.
This framework forms TON WWW: a network of interconnected web pages and services on TON, accessible through a TON crypto wallet and web browser.
TON Proxy
To access the TON network, users must connect through a specific entry point known as an “entry proxy.”
Currently, the TON Foundation provides public entry points.
These public entry points should be used with HTTP for testing purposes only, as traffic outside the TON network is not encrypted in this case.
Tech-savvy users can already set up entry proxies on their devices. In the near future, this functionality will be simplified and made available to all users via a straightforward application.
Using a Browser
Since TON Proxy supports HTTP Proxy, you can configure your browser or system settings to use a public TON entry proxy as your proxy server.
This setup allows you to access “.ton” sites directly in your browser, just like any other website.
For detailed instructions on configuring TON Proxy across different browsers, refer to the provided guide.
Wallets
Simplifying access is always a goal. Several TON wallets are working on integrating TON Proxy directly into their apps, eliminating the need for additional software.
Currently, this functionality is available via the MyTonWallet Google Chrome extension: switch to TON Proxy, and your browser will be able to access TON sites.
In the near future, this feature will also be incorporated into the standard TON Chrome Extension, Tonkeeper, and other TON wallet applications.
Upcoming Developments
We are anticipating two major updates focused on enhancing privacy and expanding decentralized finance capabilities.
TON Proxy 2.0 — Enhanced Privacy
A major concern with the current internet is that both users’ IP addresses and website IPs are exposed and easily traceable.
With the TON Proxy 2.0 upgrade, users will have the ability to set up intermediary proxy nodes within the TON network. This update introduces garlic routing, which routes data through a series of intermediary nodes, effectively concealing the IP addresses of both users and sites.
Anyone will have the opportunity to operate these intermediary nodes, similar to TOR or I2P. This will enable widespread experimentation with the technology.
Site Security
Many websites, especially beyond the homepage, rely on services like CloudFlare or Akamai to obscure their IP addresses and defend against DDoS attacks and breaches.
While these services are effective, they are centralized commercial entities. These companies control a significant portion of the internet, and a major issue with one can result in widespread outages, impacting a large part of the web.
We believe that utilizing decentralized nodes via TON Proxy offers a more robust and reliable solution for protecting a site’s IP address.
User Privacy Protection
Typically, a user’s IP address is visible and can be exploited by hackers or corporations to gather extensive information about online activities. Corporations can track your browsing history even without user accounts by analyzing IP addresses.
TON Proxy addresses this issue by rerouting internet traffic through multiple intermediary proxies, ensuring that the destination site or service cannot see your real IP address.
With the introduction of TON Proxy 2.0, complete anonymity will be achievable within the TON network.
TON Proxy 3.0 — Advancing Decentralized Finance
In the third phase, the decentralized Toncoin economy will be integrated with intermediary TON Proxies to enhance user privacy and site security.
Payments will be processed through the Payment Network technology, developed in Q2 2022. Intermediary proxy nodes will earn micropayments for handling internet traffic — for instance, for each 128 KiB package — which will be deducted from users’ crypto wallets.
This decentralized payment model will allow independent administrators to manage intermediary proxy nodes globally, improving the network’s efficiency, scalability, and stability.
We believe that the lack of financial incentives has hindered the scalability of networks like I2P and TOR over the past 20 years.
Conclusion
The current internet operates on protocols dating back to the 1990s, and some even from the 1980s. While these foundational technologies have served us well, they are increasingly inadequate in addressing modern privacy and security demands.
As technology becomes more integrated into our daily lives — through surveillance cameras, fitness trackers, and automated checkout systems — the risks to personal information grow. Misuse of this data can lead to severe consequences, including threats to personal safety.
Moreover, the concentration of power among major corporations has made the internet more fragile and privacy-compromising, as vast amounts of user data are collected, sold, or exposed in data breaches.
Today, we take a significant step towards addressing these challenges by introducing the TON network, featuring TON Proxy and TON Sites with TON DNS integration. These decentralized, secure, and user-friendly services offer a superior alternative to the traditional web.